Why you should use your PC for hosting???
- Free of cost
- Total over control in your hand
- You can use it for fun(for experiments).
- Hosting means your PC is running 24×7 non-stop.If somehow your PC is shutdown or powered off then your website is offline from all over internet.
- Running your PC 24×7 for website is not a good idea.
- If your PC got corrupted then your website will too.
- There is no surety that your ISP will providing 24×7 internet without disconnection and same applicable for power .
So,Let’s start our hosting :
Here I’m using WAMP server , you can download latest version form here.and install it.after then add the security exception for Apache in Windows Firewall.
Now after installation :
1. Go to your browser and type localhost .Just only to make sure that you properly install and configured WAMP.(If localhostopens WAMP homepage in your browser it means you are ready to rock with your PC).
2. Now click on WAMP icon placed in taskbar like this and then click on www directory.
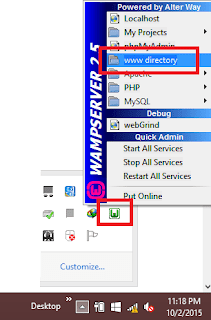
3. Copy your website content and pages in www directory.Example :I made a webpage and copied it in www directory.
4. Now go back to your browser and type localhost/mywebsite(replace mywebsite with your website page)in URL bar.You see your website like this :
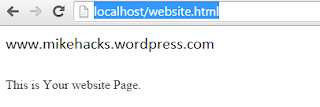
Congrats your website is up and running.
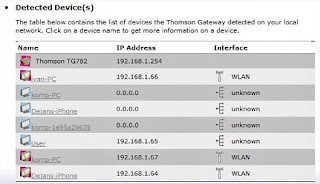
But this is only works on LAN .If you want to host it on WAN then you need a static ip(i.e. A static IP address is a number (in the form of a dotted quad) that is assigned to a computer by an Internet service provider (ISP) to be its permanent address on the Internet.).Use your IP in URL bar instead of localhost then it will works on WAN means you can access your website anywhere in the world.
Troubleshooting :
- Make sure you installed WAMP correctly
- If you are unable to see localhost page then just turn off your firewall and then try.
- If your website is not responding then please double check URL (discussed in step 4)